Amazon Web Services is one of the most popular choices for cloud computing nowadays. You may find a corresponding solution in AWS for almost any particular demand for your service. However, it can be a little bit intimidating for new learners to start. This article will guide you through the setup of a server with AWS, often referred to as an EC2 instance, and provide a high-level view of the AWS architecture.
We picked EC2 as an example because it's the foundation of many other services. And it features the most common demand: spinning up a server of which you have full control. From there, you can build and host your brilliant ideas. EC2 also involves almost everything AWS can provide but we don't necessarily need to use all of them right away. This opt-in strategy allows us to make our service cost-efficient, secure, reliable and has the ability to scale.
A Note On Cost
AWS has a flexible pricing strategy depending on the server tiers and services attached. However, please be mindful of the potential cost. AWS often provides free services for newly registered users for the first year or so (varies from time to time) for low-tier servers. You can follow this article using the free-tier service with no problem. And even if you're not free-tier eligible user, you will not be charged until launching the service.
For more details on pricing, please refer to the official documentation: https://aws.amazon.com/pricing
Spinning Up A Server With AWS EC2
This section is a step by step tutorial on how to spin up a server using AWS EC2.
EC2 Dashboard
After logging into your AWS account, navigate to the EC2 dashboard through Services -> Compute -> EC2. In the dashboard there will be a lot of information, but we don't need to worry about it for now. All you need to do is click the Launch Instance button.
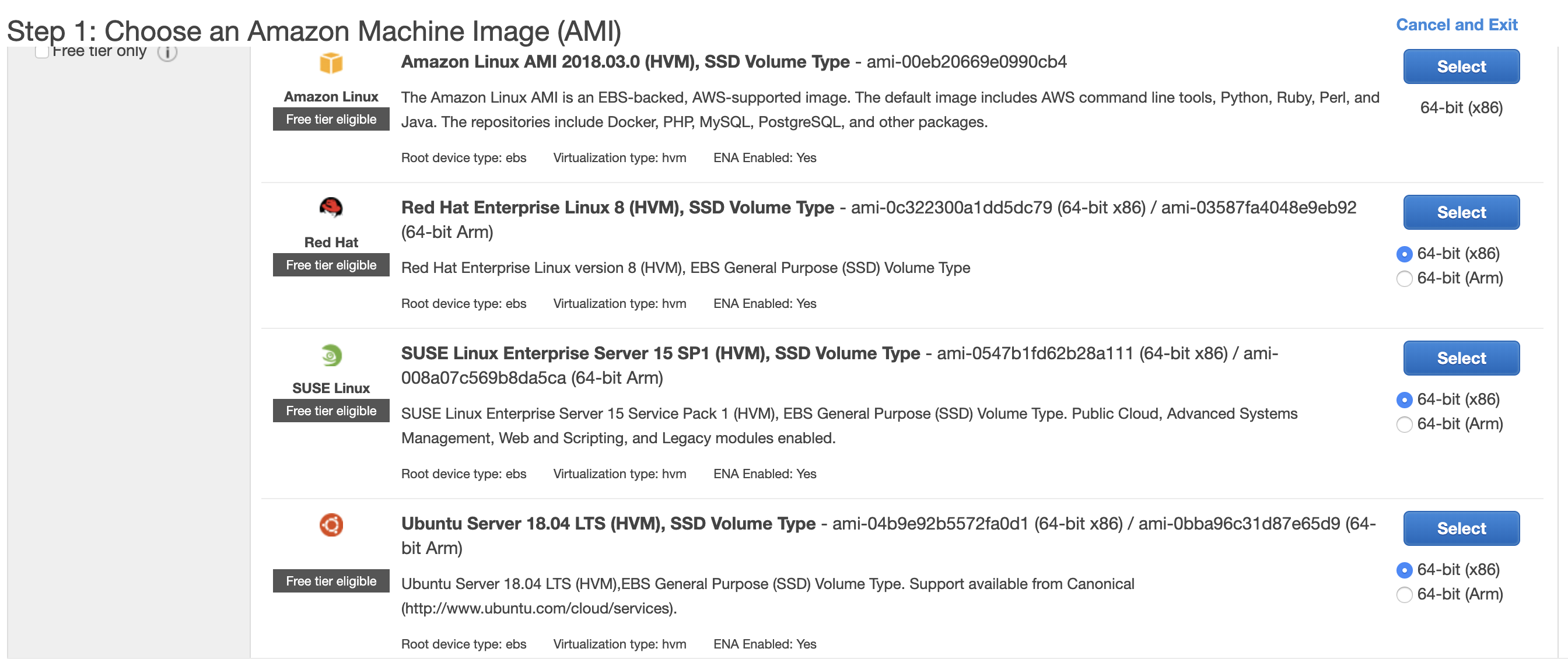
Choosing An Image
You will navigate to a page titled Step 1: Choose an Amazon Machine Image (AMI). From there, you may select an operating system of your choice, EC2 supports most of the common options out there. We will use the latest version of Ubuntu as an example. Click the Select button and you will navigate to the next page.
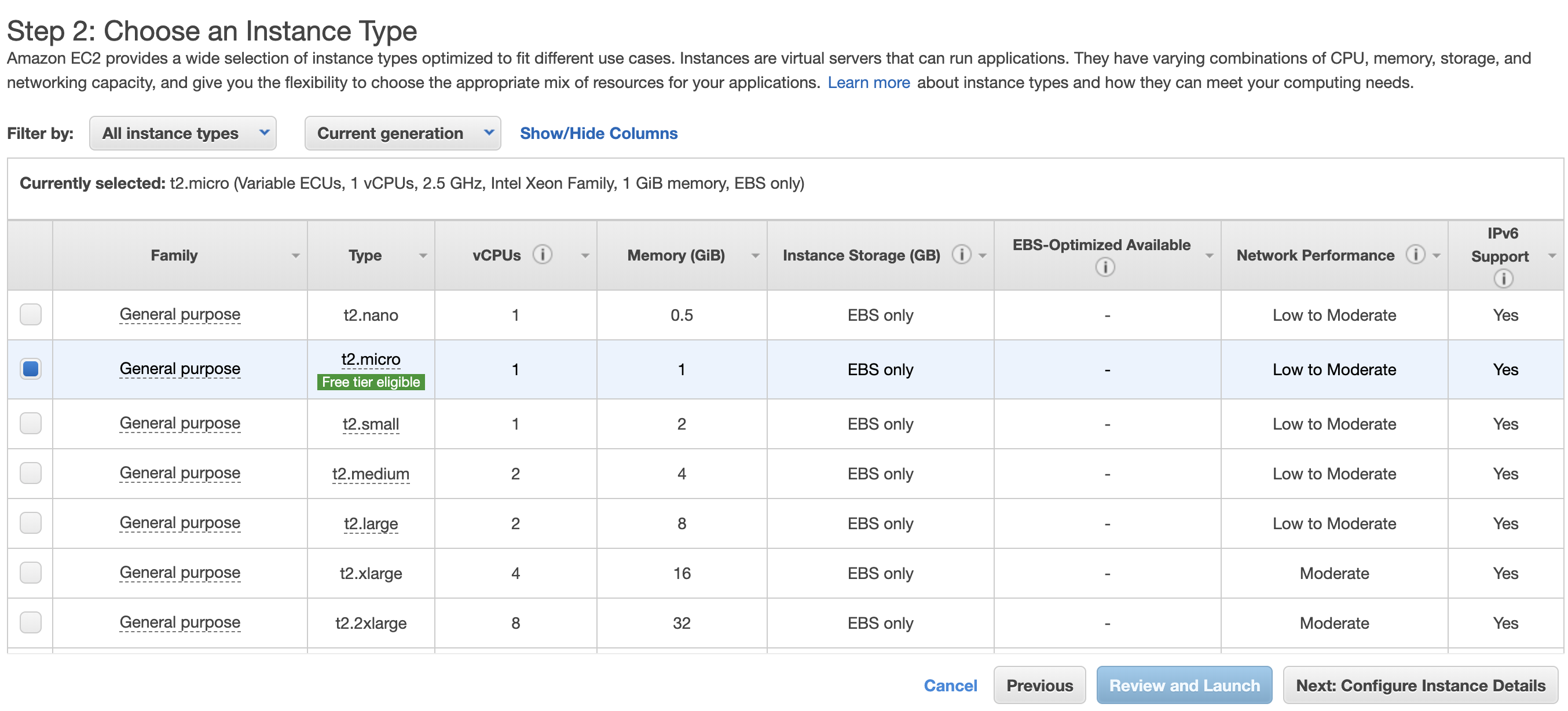
Choosing an Instance Type
In this page, you will be presented by a list of server options differed by CPU cores, memory size, disk type, network speed etc. The free tier servers are usually marked as "free tier eligible". Most of the configurations are intuitive, and there is often an information tooltip on certain terminologies. Since we are only introducing the architecture, we will use the free-tier server, t2-micro, for demonstration. Next, we click the Next: Configure Instance Details button, not the Review and Launch button.
Configuring Instance Detail
In this page, you will be asked to configure many options, some of which are AWS specific and can be confusing. These are more advanced features and we should just leave them as default for now. We can go to the next step by clicking the Next: Add Storage button.
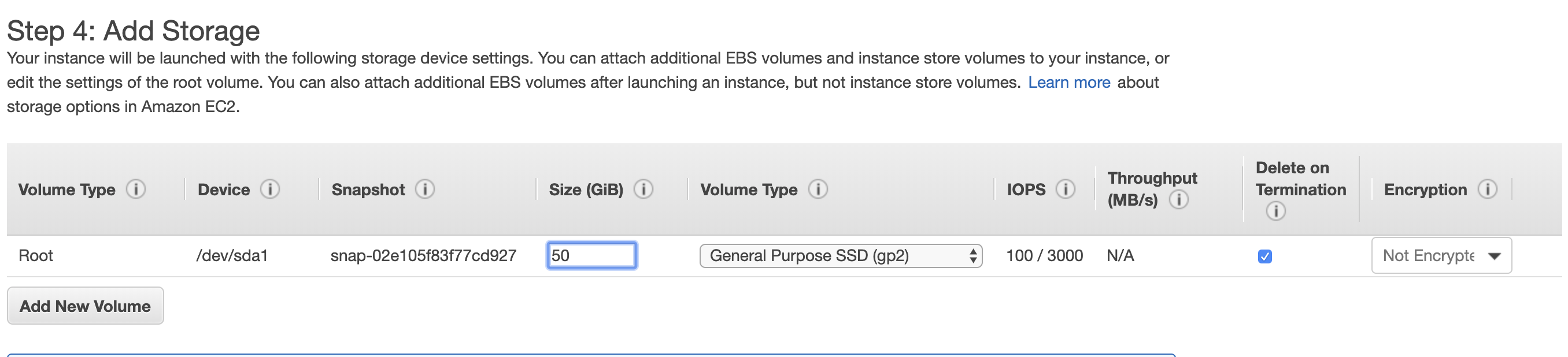
Adding Storage
In this page, you can specify the disk space you require for your server. Depending on the server tiers, you may have different storage options. The default option: General Purpose SSD would suffice the most common use cases. Note that more advanced options, such as Provisioned SSD, encryption etc. cost more money. Free-tier servers may also restrict the disk size (~200GB) in order to remain free.
Click the Next: Add Tags button to proceed.
Adding Tags
You can specify any key-value pairs known as tags in your EC2 instance. It can be useful for filtering in different metrics. Although it is totally optional, we highly recommend that you add at least one tag, the Name tag. This tag will be used in the EC2 dashboard directly and will help you identify what the instance is for when you have multiple ones running.
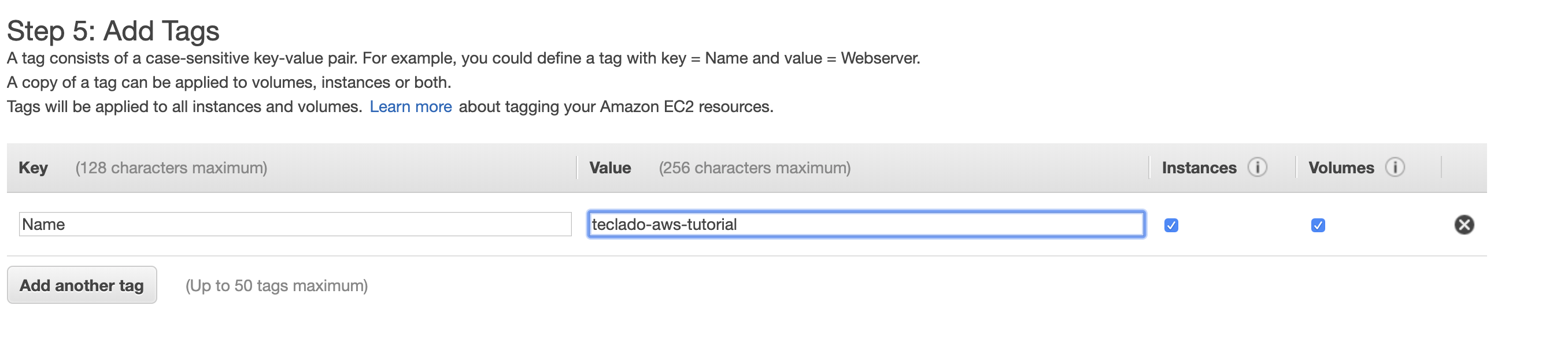
Then we click the Next: Configure Security Group button to proceed to the final configuration.
Security Group
This is one of the most important feature of AWS. A security group contains a set of rules on both incoming and outgoing traffic. You can specify what protocol you want to allow, as well as the port and IP address or range. It is very similar to a firewall, but with additional advantages. It allows you to reuse the rules for other instances by simply attaching them to the same security group. You can also attach multiple security group to one instance. It's a bit like multiple inheritance in Object Oriented Programming.
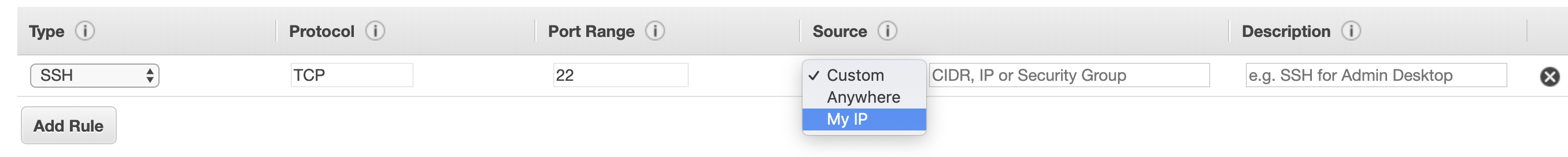
A common scenario I can relate to is to only allow SSH from my own IP and only allow HTTP/HTTPS on certain ports where your service is exposed to public.
Launching The Instance.
The final step is to review and launch the instance. Check if any of your configurations have changed unexpectedly, and proceed to launch when everything is correct. You'll be prompt by a popup window to select or create a key since AWS uses SSH by default.
The EC2 instance may take a while to boot, since a lot of configuration is taking place. Notice that in the EC2 dashboard, you can locate your instance using the Name tag, and when the status shows "2/2 status check passed", you may proceed to connect to your server with the key. You will be able to securely connect to the server using the user named ubuntu:
ssh -i <path/to/your/key> ubuntu@<ip>
Note that the ubuntu is not the root user but it does have sudo privilege. In short, it's a properly pre-configured user that meets the most common requirements.
Wrap Up
We just went through the set up procedure, which involves a lot of steps. As you get more familiar with it, it becomes more of a routine. If you're new, I would recommend go over this procedure over again all by yourself.
Of course, remember to Terminate the existing instances to avoid being charged (Stop would only halt the server and you will still be charged).
Advanced Concepts
In this section, we will cover slightly more advanced concepts within AWS. It will be a very brief introduction just to shed some light on how powerful it can be.
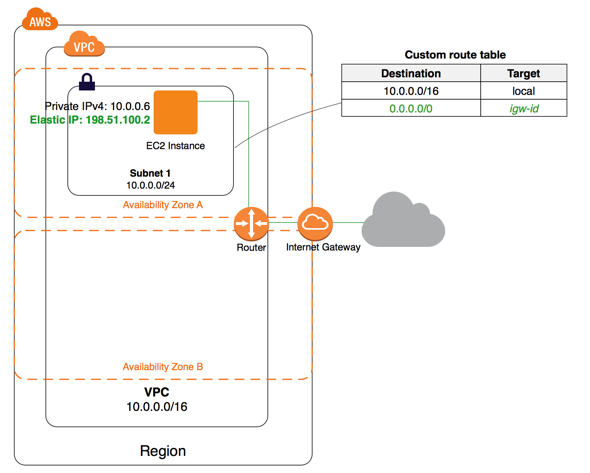
Virtual Private Cloud
As we introduced earlier, security groups can protect your servers as a firewall. However, in production, we would typically want more safeguard that a firewall. For instance, databases should be kept in a more private network, which would ideally be isolated from the public. This is when Virtual Private Cloud (VPC) comes into play. A VPC usually consists of several subnets. When creating a subnet, you can specify the public accessibility and decide whether it should be reachable from outside of your VPC. A typical setup would be: hosting your database in a private subnet and the API in a public subnet. Then your API would be assigned a public IP address while your database would only have a private IP address (something like 10.0.0.1). Then you need to define the routing table to allow traffic from your public subnet to your private subnet. In this way, users would only talk to your API, and then the API can communicate to your database in a safe, defined manner.
Availability Zone
Within a VPC you may define a few Availability Zones (AZs), which guarantees physical isolation. Since AWS provides abstracted servers, meaning that they may or may not split a powerful server or a disk into several parts and offer them as separate servers/disks, then there is a chance that a user might be running two logically unrelated servers on one machine.
It helps to reduce the cost and make the most out of each server. However, in production, it might not be good enough. Although AWS is rarely down, you might just not want to take that risk. That's when Availability Zones come into play.
When launching an instance, especially a production database, you may opt-in to the multi-AZ option (multiple availability zones). It requires you to define at least two AZs. If your instance is attached to multiple AZs, when one of the servers goes down, the one in the other AZ will take its place and keep your service up running.
AWS Terms Cheatsheet
- AWS: Amazon Web Services - a collection of services by Amazon.
- EC2: Elastic Cloud Computing - aka. servers
- RDS: Relational Database Service - aka. SQL databases
- AMI: Amazon Machine Images - server Images (Ubuntu, Windows Servers, etc.)
- EBS: Elastic Block Storage - disk
- VPC: Virtual Private Cloud - a logical network where you may define public accessibility
- IAM: Identity & Access Management - encapsulated user groups
- Security Group: Encapsulated firewall
- IGW: Internet Gateway


